INSNAPSYS Knowledge Hub
Discover a treasure trove of knowledge and expertise as we delve deep into industry topics, share best practices, and explore the future of technology.

Most Popular
The Autonomous Enterprise: How Agentic AI is Reshaping Work, Security, and Operations
It’s Sunday night. A CISO’s phone buzzes with another security alert. Four hours later, the verdict is a false positive-the 47th this month. It’s Monday morning. An IT help desk is flooded with calls: the CRM is slow, the campaign system is down, and the finance...
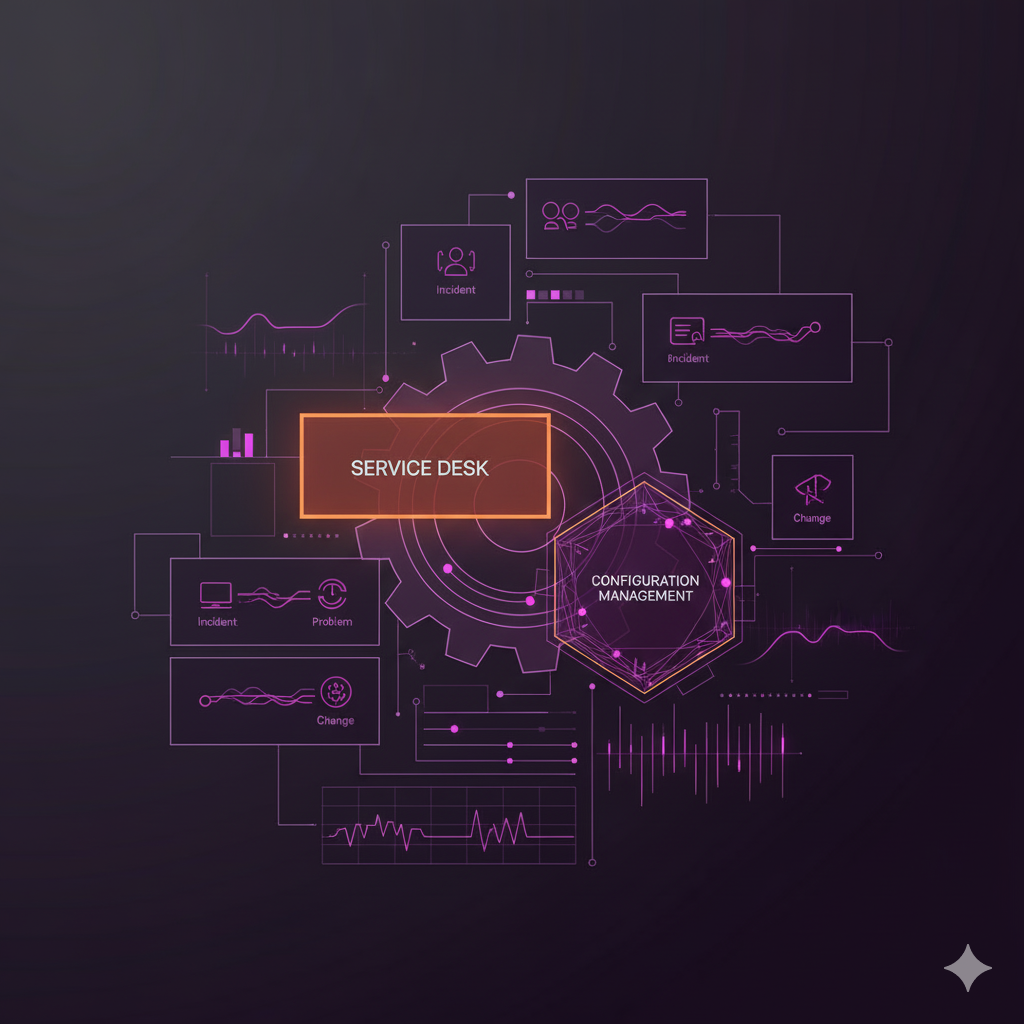
Predictive ITSM: From Reactive Support to Proactive Operations
From Reactive to Predictive ITSM: How Modern Service Management Is Evolving For decades, IT Service Management has relied on a reactive, ticket-driven approach. Incidents are logged after failures occur, changes are reviewed after disruptions, and success is...
IT Asset Management Challenges in Enterprises: Building a Future-Ready ITAM Function
Introduction As enterprises scale across hybrid infrastructure, distributed teams, and cloud-native environments, IT asset management challenges in enterprises are becoming more complex and business-critical. IT Asset Management (ITAM) has evolved from a...
The Zero Trust Trap: Three Invisible Cracks That Sink Enterprise Security
The Monday Morning Discovery Picture this: It's Monday morning at a thriving financial services firm. The CISO walks into the office feeling confident. After eighteen months and millions invested, their Zero Trust rollout is "complete." The board presentation went...
- Agentic AI
- AR & VR
- Cloud Computing
- Cybersecurity
- Data Security
- Development
- Django Development
- Generative AI
- IT Asset Management
- ITSM
- Laravel Developers
- Machine Learning
- MERN Stack Developer
- MERN Stack Developers
- Node Js developer
- Python developers
- React JS Developers
- Remote developers
- Robotic Process Automation
- Slider
- Voice Agent
IT Service Management: Transforming IT from Cost Center to Strategic Partner
Introduction: When IT Works, Everything Works Picture this: It's Monday morning. Sarah from marketing can't access the campaign management system. The sales team's CRM runs painfully slow. Finance is locked out of their reporting dashboard. Meanwhile, the IT help...
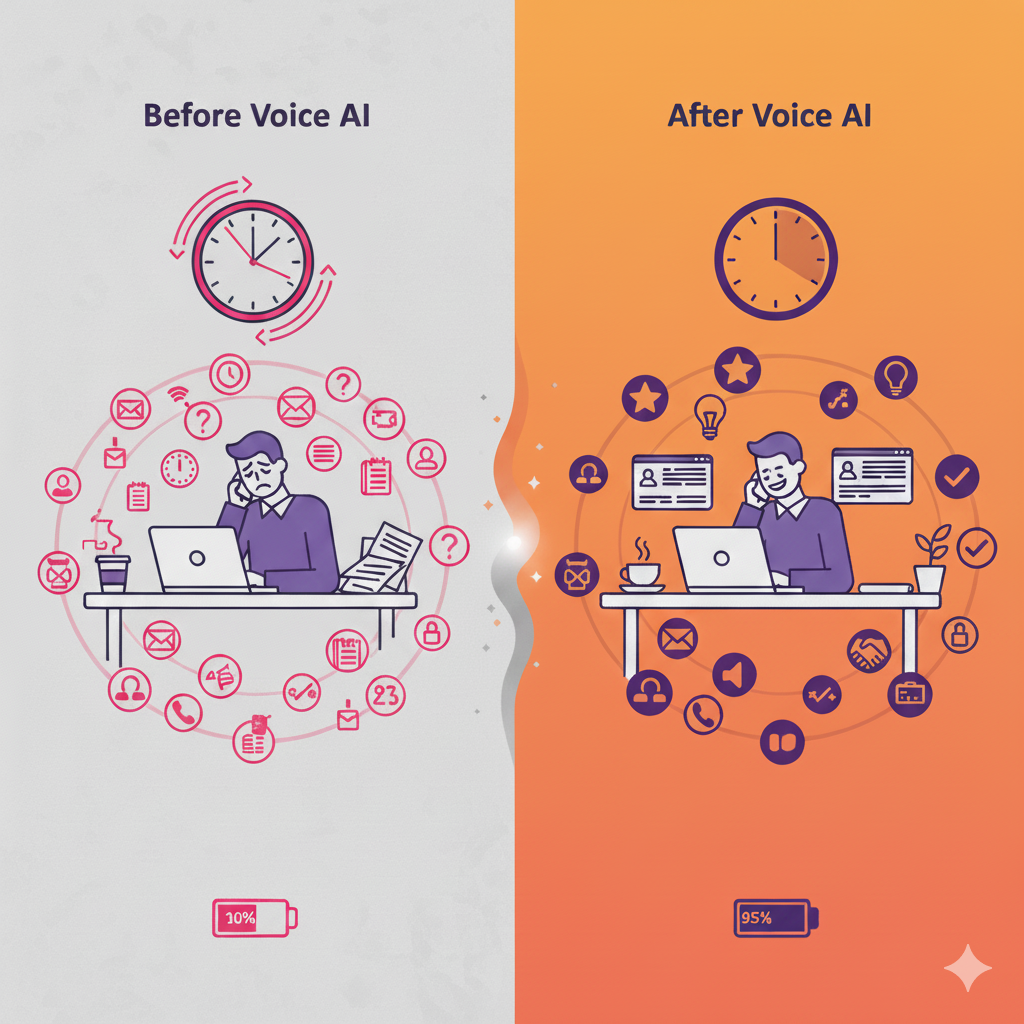
Why Your Next Hire Might Be an AI Voice Agent (And Why That’s Actually Good News)
The hiring manager's nightmare hasn't changed in 20 years. The solution finally has- A voice agent for recruiting. It's 3 PM on a Tuesday, and Sarah, a hiring manager at a mid-sized tech company, is staring at her inbox. 147 applications for a single role. She...
Voice Agent for pre-screening candidates
Discover how AI-powered Voice Agent transforms enterprise recruitment by automating candidate screening while elevating recruiter capacity
Agentic AI in Enterprises: Transforming Workflows & Efficiency
Discover how Agentic AI is transforming finance, SaaS, HRTech, real estate, and more. From automating manual tasks to enabling intelligent efficiency, learn how enterprises are adopting AI agents to drive outcomes, not just tasks.
The Benefits of Working with a Dedicated Laravel Developer
When you decide to hire dedicated Laravel developers, you're taking a major step toward ensuring your project is in capable hands. Moreover, you are saving your business from falling behind. How? Here are a few reasons: According to McKinsey, over 87% of...
Why You Should Hire Dedicated React JS Developers
Are you wondering why ReactJS has become a go-to choice for web development? Well, the answer lies in what ReactJS brings to the table. ReactJS benefits include not only its efficiency but also its ability to create dynamic and responsive user interfaces that...
Our Crowd-Favorite Blogs
Predictive ITSM: From Reactive Support to Proactive Operations
From Reactive to Predictive ITSM: How Modern Service Management Is Evolving For decades, IT Service Management has relied on a reactive, ticket-driven approach. Incidents are logged after failures occur, changes are reviewed after disruptions, and success is...
IT Asset Management Challenges in Enterprises: Building a Future-Ready ITAM Function
Introduction As enterprises scale across hybrid infrastructure, distributed teams, and cloud-native environments, IT asset management challenges in enterprises are becoming more complex and business-critical. IT Asset Management (ITAM) has evolved from a...
The Zero Trust Trap: Three Invisible Cracks That Sink Enterprise Security
The Monday Morning Discovery Picture this: It's Monday morning at a thriving financial services firm. The CISO walks into the office feeling confident. After eighteen months and millions invested, their Zero Trust rollout is "complete." The board presentation went...
Hire Top Remote Developers at INSNAPSYS
Bring dedicated remote developers onboard your project within 48 hours. Make sure our developers are the right fit for your project with the risk-free 1-week trial. If you ever find that a developer isn’t meeting your expectations, you can request a replacement or end the contract with zero penalties.