The Monday Morning Discovery
Picture this: It’s Monday morning at a thriving financial services firm. The CISO walks into the office feeling confident. After eighteen months and millions invested, their Zero Trust rollout is “complete.” The board presentation went brilliantly. The consultants have packed up and left.
Then the phone rings.
A lateral breach. An attacker who shouldn’t have been able to move past the initial entry point has somehow hopscotched across seventeen different systems, extracting customer data from servers that were supposedly “segmented” and “protected.” The security team scrambles. How did this happen? Wasn’t Zero Trust supposed to prevent exactly this scenario?
Welcome to the most dangerous moment in cybersecurity: the illusion of safety.
The Invisible Cracks
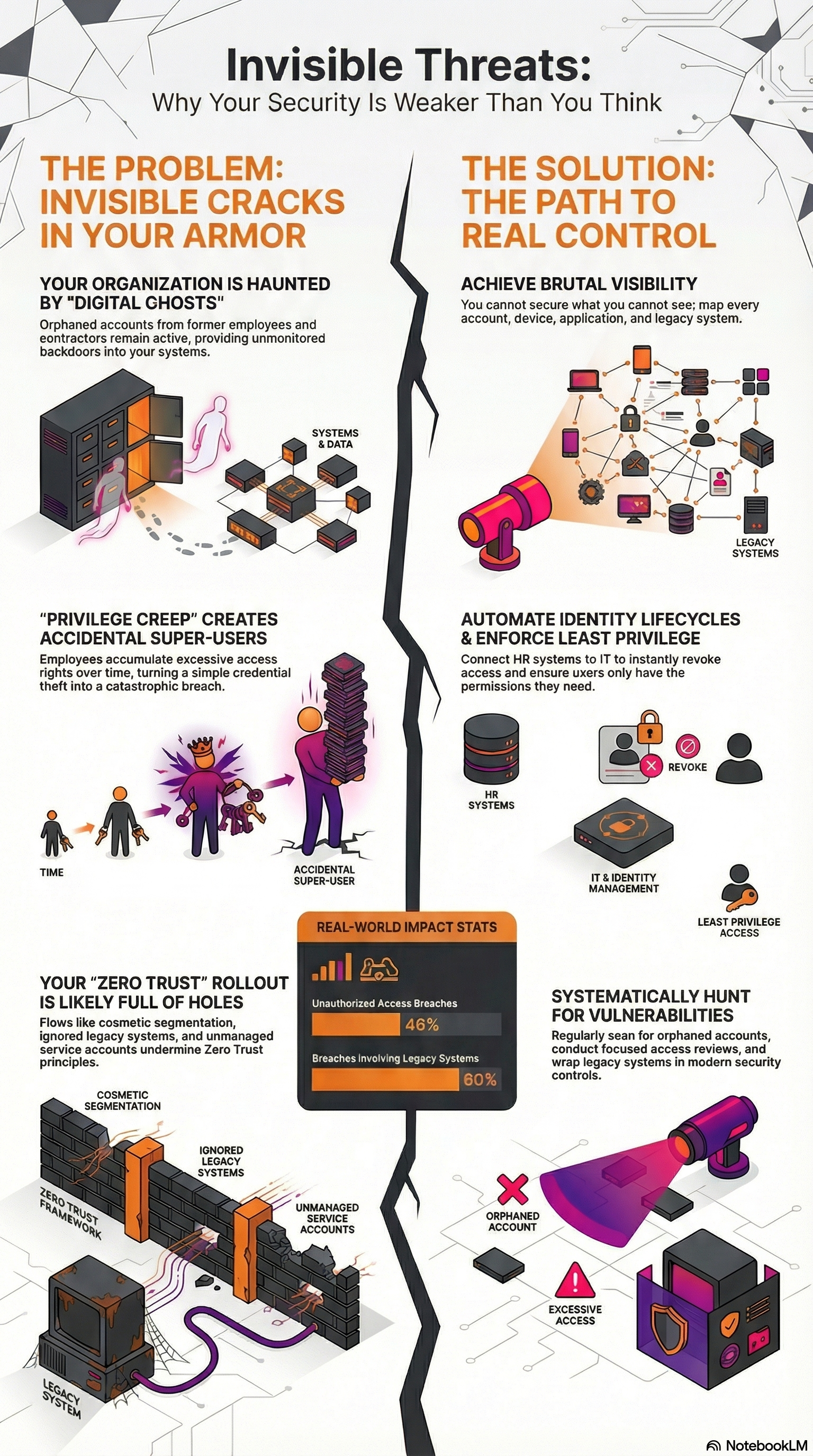
Zero Trust isn’t failing because the concept is flawed. It’s failing because enterprises are making three critical mistakes that transform rock-solid security architectures into Swiss cheese. These aren’t exotic edge cases or theoretical vulnerabilities. They’re happening right now, in organizations just like yours.
Mistake #1: The Segmentation Mirage
Here’s what happens: A company declares they’ve “implemented microsegmentation.” They’ve carved their network into neat little zones. Applications here, databases there, users somewhere else. On paper, it looks beautiful. In reality, they’ve built invisible highways for attackers.
The problem? Most organizations approach segmentation like they’re dividing a pizza-big, chunky slices that still leave too much exposed. Traditional segmentation projects often start with user identity, when instead they should focus on applications and workloads first. This creates a fundamental disconnect.
Imagine building a fortress but leaving the servant’s entrance wide open because you forgot it existed. That’s what poor segmentation does. Enterprises segment their primary applications but overlook the forgotten internal tools-the HR portal that hasn’t been updated since 2018, the backup application running quietly in the corner, the monitoring dashboards that everyone can somehow access.
When microsegmentation is combined with Zero Trust, attackers who gain initial entry encounter isolated systems and restricted pathways. But when it’s done badly? They find themselves in a maze where every wrong turn still leads somewhere valuable.
The real killer? Many organizations don’t plan accurately for the duration and complexity of microsegmentation projects, leading to unrealistic expectations and shortcuts. Teams get exhausted halfway through. They draw arbitrary boundaries based on convenience rather than threat modeling. The result looks secure but crumbles under pressure.
Mistake #2: The Authentication Theater
Walk into most enterprises implementing Zero Trust and ask about their authentication strategy. You’ll hear confident talk about multi-factor authentication, single sign-on, identity providers, and continuous verification. It sounds impressive. It might even be working-for about sixty percent of their environment.
But here’s the uncomfortable truth: authentication chains are only as strong as their weakest link, and most enterprises have dozens of weak links they don’t even know about.
Consider the service accounts running silently in the background. The API keys embedded in legacy scripts. Service accounts and credentials embedded in scripts have excessive permissions that are retained indefinitely, creating security blind spots. These aren’t users logging in through your beautiful new identity management system. They’re automated processes operating with God-mode privileges, never challenged, never verified, and absolutely never doubted.
Then there are the “temporary” workarounds. You know the ones-the emergency access panel that IT created two years ago “just in case,” the shared administrator passwords stored in that Excel sheet, the remote desktop protocol connections that bypass your shiny new Zero Trust gateway because “this one legacy application absolutely needs it.”
Older protocols like RDP or VNC lack critical security protections like endpoint verification and encryption, yet organizations continue using them, often without realizing they’ve created an authentication bypass that renders their Zero Trust investment nearly useless.
The authentication chain breaks down further when you consider the human element. Nobody wants to admit this, but when users aren’t satisfied with the tools required or with their experience accessing resources, they’ll find workarounds. Too many verification steps? Employees will find the path of least resistance. Too much friction? Shadow IT blooms like weeds in spring.
Mistake #3: The Legacy Blind Zones
Now we arrive at the elephant in every enterprise data center: legacy systems. Not the systems you talk about in meetings. The ones you hope nobody asks about.
Every organization has them. That ancient ERP system running the finance department. The manufacturing control interface that was state-of-the-art when flip phones were revolutionary. The customer database that “we’ll migrate next quarter” for the past three years.
Research has shown that 80% of security breaches involved legacy systems operating under traditional trust models. These systems were built in an era when network location equaled trust. Get inside the perimeter, and you were assumed to be legitimate. They have no concept of continuous verification, no ability to integrate with modern identity services, and no capacity to understand what Zero Trust even means.
But here’s the truly terrifying part: disconnected applications create visibility gaps that leave security teams blind, because you can’t enforce policy on what you can’t see.
These legacy systems become black boxes. Nobody knows exactly what they’re doing. Nobody understands their full attack surface. Organizations struggle to identify and classify the data held within their legacy systems, making micro-segmentation and contextualized access extremely difficult. They just… exist. Running critical functions. Holding sensitive data. Creating gaping holes in your Zero Trust architecture.
The problem compounds when you realize these systems often can’t be easily replaced. They’re too integrated, too complex, or too expensive to rip out. So they sit there, legacy time bombs ticking away, while your modern Zero Trust security flows neatly around them like water around a rock.
The Path Forward
So what do you do? Abandon Zero Trust? Absolutely not. But you need to confront reality with clear eyes.
Start with brutal honesty. Map everything-not what you think you have, but what actually exists in your environment. Every application. Every service account. Every creaking legacy system that makes your newest team members nervous. Building a complete inventory of users, devices, workloads, and applications establishes the foundation for effective Zero Trust.
Segment strategically, not cosmetically. Don’t just draw lines on network diagrams. Think about actual threat paths. Where would an attacker go? What would they want? Build your micro-segments around protecting those targets, not around organizational convenience.
Fix your authentication foundation. Hunt down every service account, every API key, every backdoor protocol. Either bring them under Zero Trust principles or eliminate them. Implement proper access control policies to enforce least privilege principles. Yes, it’s tedious. Yes, it will break things temporarily. But the alternative is watching your Zero Trust investment crumble.
Wrap or replace your legacy. You can’t ignore those old systems. Organizations can put a Zero Trust wrapper around legacy systems, requiring authentication before traffic passes through to the legacy environment. If you can’t replace it immediately, build a secure envelope around it. Gateway it. Proxy it. Monitor it obsessively. Make it prove it’s behaving correctly, even if the system itself can’t verify its own trustworthiness.
The Real Work Begins Now
Zero Trust isn’t a destination-It’s a commitment to constant vigilance. Organizations need to understand that transitioning to Zero Trust means substantial technological and organizational changes, treated as an ongoing commitment beyond the initial setup.
The enterprises that succeed aren’t the ones with the biggest budgets or the fanciest tools. They’re the ones willing to confront uncomfortable truths about their infrastructure, admit where the gaps exist, and systematically close them-even when it’s difficult, even when it’s expensive, even when it means admitting that last year’s “completed” project needs another look.
Because in Cybersecurity, the most dangerous vulnerability isn’t in your code or your network. It’s in believing you’re safer than you actually are.